Check .lt domain
How to ensure safety on websites and e-shops?
With growing cyber threats, ensuring the security of websites and e-shops is becoming increasingly important. An insecure website can have negative consequences for a business’s reputation, customer trust, sales and business continuity.
According to Tomas Simonaitis, Head of the Technical Administration Office at the Internet Service Centre DOMREG of Kaunas University of Technology (KTU), poorly maintained websites become easy targets for cyberattacks. A website infected with malicious code can be used for phishing, leaked customer databases can end up in the hands of competitors, and personal data can be used by criminals.
Domain safety is essential
A domain is a unique internet address that helps direct internet visitors via the Domain Name System (DNS) to the servers storing the files and databases of a website, e-shop or other systems. A domain allows using an email and logging onto data repositories and other services. Like a trademark, a domain is a valuable asset that enables finding and identifying a business or product online.

Tomas Simonaitis, Head of Technical Administration Office at KTU Internet Service Centre
“If criminals manage to falsify DNS responses or even change the addresses of DNS servers through domain hijacking, it allows them to redirect website visitors to fake, often fraudulent, websites, as well as intercept emails and other services. To prevent this from happening requires ensuring the security of the domain management account, renewing the domain on time and using the DNS security extension DNSSEC,” – advises T. Simonaitis.
To prevent unauthorised interception of the domain and other services, individuals should carefully protect and not disclose the login details (username and password) to the service control panel and use two-factor authentication.
If a domain validity is not renewed on time, the domain name is placed in a one-month “quarantine” period. During this time, the same domain holder can still “restore” the domain name and retain the rights to the domain. Failure to renew on time is one of the most common reasons for the loss of domain rights; therefore, domain validity should be carefully renewed so that expired domain could not be registered by someone else and used for criminal activities.
How does DNS work and what is DNSSEC?
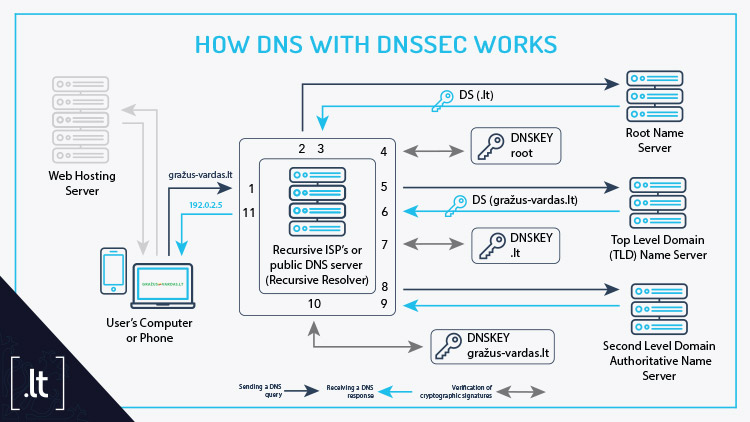
Access to the website or e-shop the user wants to visit requires writing a domain - an address - in the web browser. Then the internet service provider or a public DNS recursive resolver sends A or AAAA queries to the DNS root name server, the top-level domain name server and the DNS authoritative name server of the registrar providing services to the domain. After receiving responses from all the DNS authoritative name servers, the recursive resolver used by the user “learns” where the website is stored and directs to the server storing the website’s files and databases and from there, they are transferred to the web browser. This opens the page of the website in the browser.
According to T. Simonaitis, Head of the Technical Administration Office at KTU Internet Service Centre DOMREG, the Domain Name System Security Extension (DNSSEC) is a security extension designed to increase DNS security so that DNS query responses are authentic.
DNSSEC uses cryptographic digital signatures and a public key infrastructure to protect the transferred DNS information. Each DNS record in the domain (e.g., A, AAAA, CNAME, MX, etc.) is assigned a digital signature, which is created using the domain’s private keys. The public keys are published in special DNS records DNSKEY.
DNSSEC prevents false DNS queries
One of the most common breaches is DNS spoofing when a falsified response from the DNS authoritative name server can be submitted to the DNS recursive resolver, thereby misdirecting visitors to a fake website or e-shop.
“While using DNSSEC, forgery root, top-level domain and domain authoritative name server’s responses becomes impossible, because the cryptographic signature protects each response provided by the DNS authoritative name server. The recursive resolver checks the public keys to confirm that the information has not been altered. Thanks to the DNSSEC extension, cybercriminals have no opportunities to change and falsify DNS records by spoofing responses to the recursive resolver,” – assures T. Simonaitis.
DNSSEC also ensures email security through the transport layer security authentication (TLSA). These are DNS records specifying which certificate the email (SMTP) server is using. The server forwarding the email checks which certificate is appropriate when communicating with the recipient’s server and ensures that the email is transferred through an encrypted channel. TLSA requires DNSSEC to authenticate DNS records.
What cyberattacks does DNSSEC protect against?
DNS spoofing can be used for various cyberattacks. Criminals usually aim to redirect users to fake bank and payment websites or to create fake official websites that are malicious and designed to collect personal data or organise fake sales through falsified e-shops.
DNSSEC can be used to protect against DNS spoofing, DNS cache poisoning and interception of data through Man-in-the-Middle (MITM) attacks.
“Even though the domains protected by the DNSSEC cryptographic signatures are primarily required for high-security information systems such as banks, financial institutions, public authorities, healthcare or telecommunications companies, DNSSEC is already becoming a necessity for e-shops and even for representative websites seeking security and user trust,” – states T. Simonaitis, Head of the Technical Administration Office at KTU Internet Service Centre DOMREG.

Other measures to increase website security
Even though domain and DNS security are particularly important, other aspects of website security cannot be forgotten. To make sure that the website or e-shop is secure, and the customers feel confident about the security of their data, it is necessary to install an HTTPS protocol with SSL/TLS certificates, and constantly update the content management system (e.g., WordPress) and its components such as plugins and themes. Unused plugins or themes that may pose a risk must be removed. A two-factor authentication tool should be used to log onto the administration panel of the content management system.
The use of a firewall enabled on the website hosting server or a web application firewall (WAF) solution (e.g., Cloudflare) should protect against cyberattacks. Backups of the website should be made regularly, as well as scanning software code and taking other preventive security measures.
The number of domains is growing in Lithuania
According to the data of KTU Internet Service Centre DOMREG, the number of second-level .lt domains increased by 2.68% in 2024 and reached more than 239 thousand at the end of the year. Even though 42.2 thousand new .lt domains were created last year, 35.7 thousand were deleted.
According to the data of the Association of European Domain Registries CENTR, the .lt domain has remained the most popular domain in Lithuania in 2024, with 59% of Lithuanian domain holders having chosen it for their websites, e-shops, email and other services.
Published 2025-02-17



